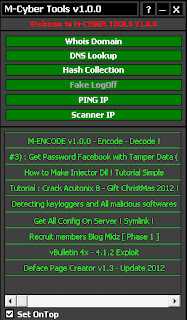
M-CybEr Tools v1.0.0
* Feature M-CybEr Tools :
- Whois Domain Tool :
- DNS Lookup Tool :
* Details :
- Name : M-CybEr Tools
- Version : 1.0.0
- Coder : Midz
- Work Good On XP OS - Support Windows 7
- DOWNLOAD M-CybEr TOOLS : CLICK HERE
- Virus Scan : http://virusscan.jotti.org/vn/scanresult/99bf762addd7d4330e6e45fcd01aa39677614b61
- Size : 136704 bytes
MD5: c5042a20d13edd63c26e58a583dbe0f2 SHA1: ccb48f215276a26688fd65d4235d467c3144eb5b